- Istio an introduction
- Getting started with Istio
- Istio in Practice – Ingress Gateway
- Istio in Practice – Routing with VirtualService
- Istio out of the box: Kiali, Grafana & Jaeger
- A/B Testing – DestinationRules in Practice
- Shadowing – VirtualServices in Practice
- Canary Deployments with Istio
- Timeouts, Retries and CircuitBreakers with Istio
- Authentication in Istio
- Authorization in Istio
- Istio series Summary
The VirtualService resource
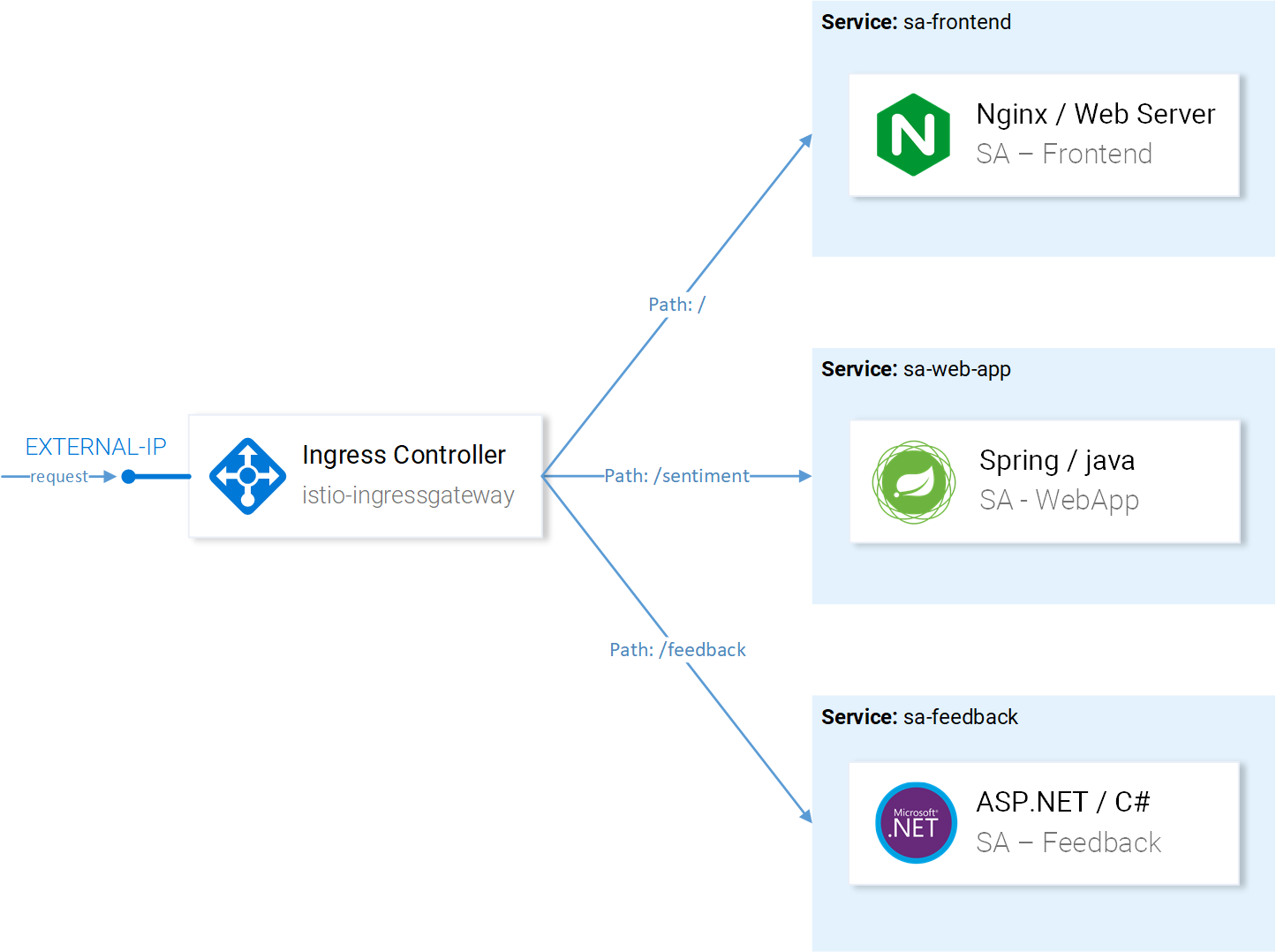
The VirtualService instructs the Ingress Gateway how to route the requests that were allowed into the cluster.
For our application requests coming through the http-gateway must be routed to the sa-frontend, sa-web-app and sa-feedback services (shown in figure 1).
Let’s break down the requests that should be routed to SA-Frontend:
- Exact path
/should be routed to SA-Frontend to get the Index.html - Prefix path
/static/*should be routed to SA-Frontend to get any static files needed by the frontend, like Cascading Style Sheets and JavaScript files. - Paths matching the regex
^.*\.(ico|png|jpg)$should be routed to SA-Frontend as it is an image, that the page needs to show.
This is achieved by the following configuration:
Additionally, important here are the following points:
- This VirtualService applies to requests coming through the http-gateway.
- Destination defines the service where the requests are routed.
Note: The configuration above is in the file sa-virtualservice-external.yaml, it contains the configuration to route to SA-WebApp and SA-Feedback but was shortened here for brevity.
Apply the VirtualService with the command below:
$ kubectl apply -f resource-manifests/istio/sa-virtualservice-external.yaml virtualservice.networking.istio.io "sa-external-services" created
Note: When we apply this resource (and actually all Istio CRD resources) the Kubernetes API Server creates an event received by Istio’s Control Plane which then applies the new configuration to the envoys (istio proxies, sidecar proxies) of every pod. And the Ingress Gateway controller is another Envoy which is configured by the Control Plane, visually presented in figure 2.
The Sentiment Analysis app is accessible on http:/{{EXTERNAL-IP}}/. If you get a Not Found status, do not worry sometimes it takes a couple of minutes for the configuration to go in effect and update the envoy caches.
Before moving into the next section generate some traffic needed to demonstrate what we get out of the box from Istio. It’s insane! Meet me in the next article!
If you enjoyed the article, please share and comment below!